Costs of security breaches due to AI use reach $4.88 million

By Mario A. Beroes Ríos- IT Business Solutions.
Hispanic American companies in general are facing an increasingly complex cybersecurity environment. This environment is preceded by an increase in threats targeted and empowered by a new ingredient, Artificial Intelligence (AI).
It is a fact recognized by several cybersecurity experts that traditional connectivity strategies, based on technologies such as Firewalls, VPNs, NACs, among others, are no longer sufficient to protect critical digital assets.
These solutions, designed for a traditional perimeter environment, are now vulnerable to a scenario where threats not only come from remote access, but worse, from within the corporate network.
Cybercriminals are evolving rapidly, becoming increasingly more attractive and targeted; they are no longer limited to mass attacks, but now use advanced tools, such as Artificial Intelligence (AI) and automation, to design targeted attacks that exploit specific vulnerabilities in organizations’ systems, even targeting users as the weakest link, whether internal, external or hybrid.
Today’s threats are not only more complex, but are specifically targeted to breach critical points of organizations. The rise of remote or hybrid working and reliance on the cloud have multiplied the risks, making a more robust secure access approach tailored to today’s environment necessary.”
The cost of cybersecurity breaches
According to data from technology company IBM, the average cost of a security breach reaches $4.88 million, a figure that increases when organizations rely solely on basic access controls.
The use of traditional tools such as VPNs, NACs, firewalls, among others, has proven to be insufficient to contain current threats, which increases the financial risk and the impact on the reputation of companies. Against this backdrop, the adoption of a secure access model based on the Universal Zero Trust Network Access (ZTNA) approach has become a key trend in the industry.
This model changes the traditional security approach, based on secure access strategies designed only for external users, allowing them to connect and then identify/authenticate, to a strategy that first validates the user and then grants access to a critical technology asset, regardless of its location (inside or outside the computer network) or the type of network used.
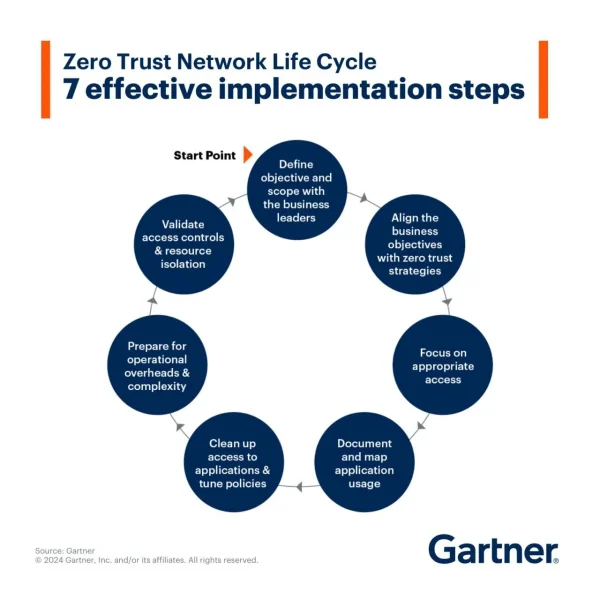
In the financial sector, access control is key to protecting business and customer information and operations. In the government sector, the adoption of a Zero Trust approach to security makes it possible to protect systems that manage strategic data and critical infrastructure.
On the other hand, companies dedicated to providing cybersecurity services insist on the need to invest in this area, perhaps the most effective way to prevent any type of attack by hackers.
In IT Business Solutions we count on the solutions that in the topic of financial cybersecurity in particular provide us with allies such as Ping Identity and Sail Point, whose features and benefits are able to offer the Universal Zero Trust Network Access (ZTNA) approach.
If you would like to learn more about cybersecurity, please visit our website: https://itbscorp.com/ ”











